How Does Extensible Authentication Protocol Work
Protected Extensible Authentication Protocol PEAP PEAP like all other EAP methods determines how authentication materials are protected. The supplicant is needed because it initiates the connection by engaging in an Extensible Authentication Protocol EAP transaction between the supplicant and the controller or switch.
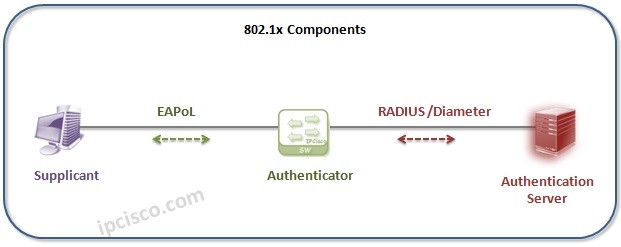
Eapol 802 1x Extensible Authentication Protocol Over Lan Ipcisco
Its major scope is wireless network communication such as access points used to authenticate client.

. Im purposely using the word Materials as there is nothing saying the authentication mechanism has to be a usernamepassword. One of these is Extensible Authentication Protocol Transport Layer Security EAP-TLS a protocol that is popular for local area networks. How does Passwordless EAPExtensible Authentication Protocol operate.
The Extensible Authentication Protocol EAP is a protocol for wireless networks that expands on authentication methods used by the Point-to-Point Protocol PPP a protocol often used when connecting a computer to the Internet. The Extensible Authentication Protocol EAP is a protocol for wireless networks that expands the authentication methods used by the Point-to-Point Protocol a protocol often used when connecting a computer to the internet. As you say there are a variety of EAP protocols.
You could call EAP a protocol or you could call it a framework of protocols where each variant like EAP-FAST is a protocol. How does Passwordless EAPExtensible Authentication Protocol operate. The authenticator in the middle is the AP or WLC which blocks all traffic except for authentication traffic.
The standard authentication protocol used on encrypted networks is Extensible Authentication Protocol EAP which provides a secure method to send identifying information over-the-air for network authentication. The supplicant gathers the credentials of the user together in a way that corresponds with what 8021X can read. And the authentication server which gives permission.
EAP is used primarily in wireless communication for authentication among clients and a wireless LAN. The authenticator which grants access. For more information see.
If the client certificate is not installed authentication fails. The supplicant which requires access. PEAP provides a transport layer security structure where it is.
Extensible Authentication Protocol EAP is an authentication framework not a specific authentication mechanism frequently used in wireless networks and point-to-point connections. You could follow this solution to fix this issue. The Extensible Authentication Protocol EAP is a protocol for wireless networks that expands on authentication methods used by the Point-to-Point Protocol PPP a protocol often used when connecting a computer to the Internet.
EAP is used on encrypted networks to provide a secure way to send identifying information to provide network authentication. Extensible Authentication Protocol is an authentication resource for wireless networks and point-to-point setups. LEAP PEAP EAP-FAST EAP-TLS etc.
As a general framework this protocol is useful in many different variations. When the authentication server verifies the credentials of the end user the authenticator unblocks the traffic and permits all wireless traffic. Select VPN Client-To-Site VPN from the VPN menuYoull need to choose User Authentication in the Settings sectionLocal or external authentication is availableClick on Step 2 of the Local Certificate list and use the Certificate to which you created it from the listA VPN certificate may be eg v.
The authentication server asks the access point for proof of the validity of the ID. EAP methods operate within the EAP framework to support a variety of authentication techniques. Extensible Authentication Protocol EAP is an authentication framework that is used in local area networks LANs and dial-up connections.
This problem occurs if the client certificate is missing from Certificates - Current UserPersonalCertificates. Extensible Authentication Protocol EAP is a point-to-point P2P wireless and local area network LAN data communication framework providing a variety of authentication mechanisms. The authentication is based on a three-party model.
The authentication server asks the access point for proof of the validity of the ID. Extensible Authentication Protocol Transport Layer Security EAP-TLS is an IETF open standard thats defined in RFC 5216More colloquially EAP-TLS is the authentication protocol most commonly deployed on WPA2-Enterprise networks to enable the use of X509 digital certificates for authentication. Protected Extensible Authentication Protocol PEAP is an 8021X authentication type for wireless LANs WLANs.
The EAP protocol can support multiple authentication mechanisms without having. 8021X is the standard that is used for passing EAP over wired and wireless Local Area Networks LAN. For example an administrator who requires digital certificate-based authentication might deploy the EAP-TLS method.
Authenticate a user before allowing them access to a wireless network. EAP is used to authenticate simple dialup and LAN connections. It provides some common functions and negotiation of authentication methods called EAP methods.
The Extensible Authentication Protocol EAP enables extensible authentication for network access. The authentication server is usually a RADIUS server. The supplicant has an identity and some credentials to prove that it is who it claims to be.
PEAP provides strong security user database extensibility and support for one-time token authentication and password change or aging. Click to see full answer. Each one works differently but they all do the same thing.

What Is Extensible Authentication Protocol Eap And How Does It Work The Security Buddy

3 Introduction To Extensible Authentication Protocol Eap Youtube

Figure 4 From Extensible Authentication Protocol Eap And Ieee 802 1x Tutorial And Empirical Experience Semantic Scholar
No comments for "How Does Extensible Authentication Protocol Work"
Post a Comment